Hasura allows you to define role-based access control rules for each of the models/tables that you use. Access control rules help in restricting querying on a table based on certain conditions.
Hasura table of content
Hasura – Authorization
Roles
Every table/view can have permission rules for users based on their role. By default, there is an admin role that can perform any operation on any table. You can define roles and then create permissions for each of those roles.
Permission rules can also refer to as session variables. Session variables are key-value pairs in the JWT custom claims. These session variables are used to defined permissions for rows and columns of a table. Permissions are essentially a combination of boolean expressions and column selections that impose constraints on the data being returned or modified.
Row level permission
Limit access to a subset of the rows in the table based on this permission. Row-level permissions are essentially boolean expressions that, when evaluated against any row, determine access to it. These permissions are constructed from the values in columns, session variables and static values to build this boolean expression.
Column level permission
For the rows that are accessible based on the above, limit access to a subset of the columns based on this permission rule.
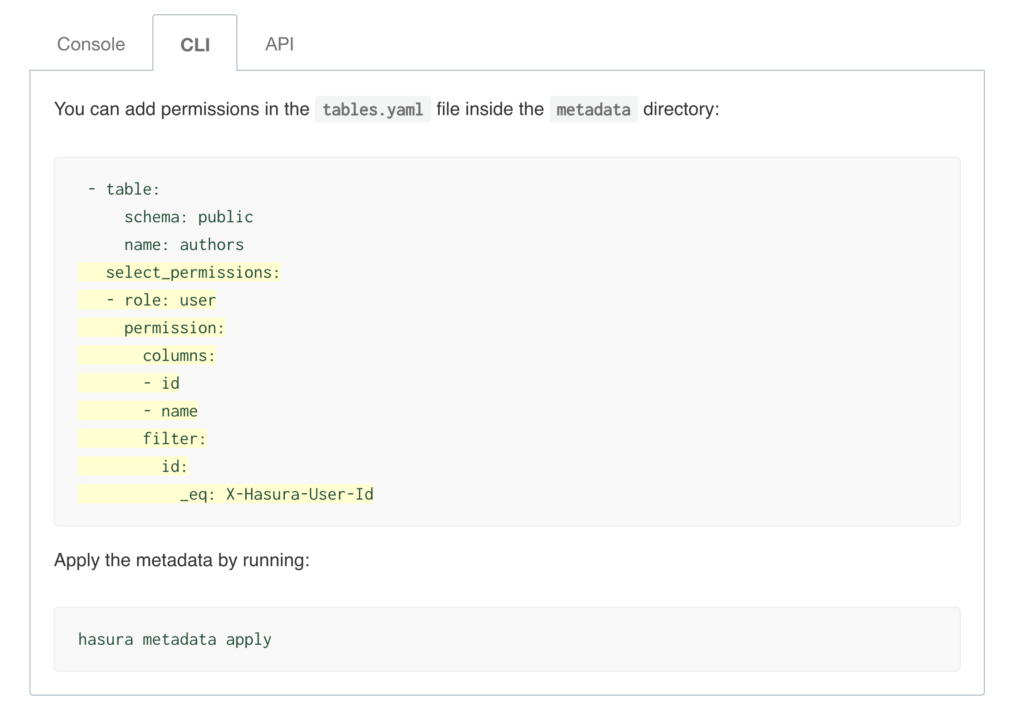
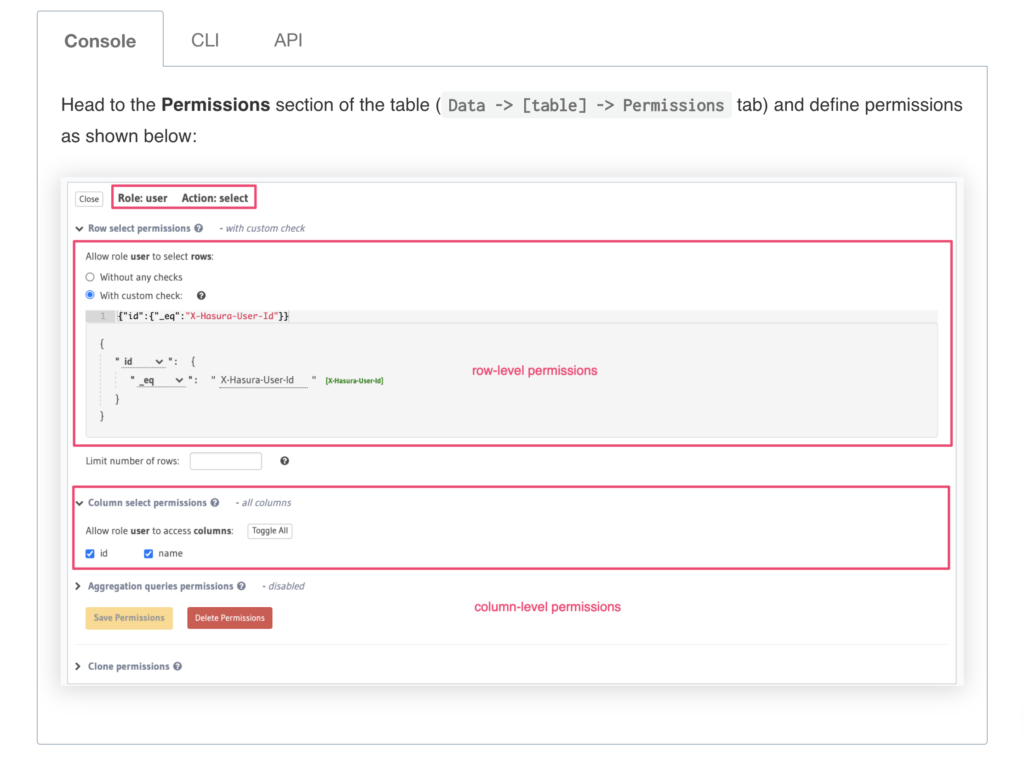
You can also allow users to have access all rows and all columns of a particular table. You can do that by selecting “Without any checks” option
Hasura – Triggers
Has
Hasura – Deployment
Deploying or Running Hasura on AWS ECS Fargate
Create a Task Definition
- Use the right hasura docker image
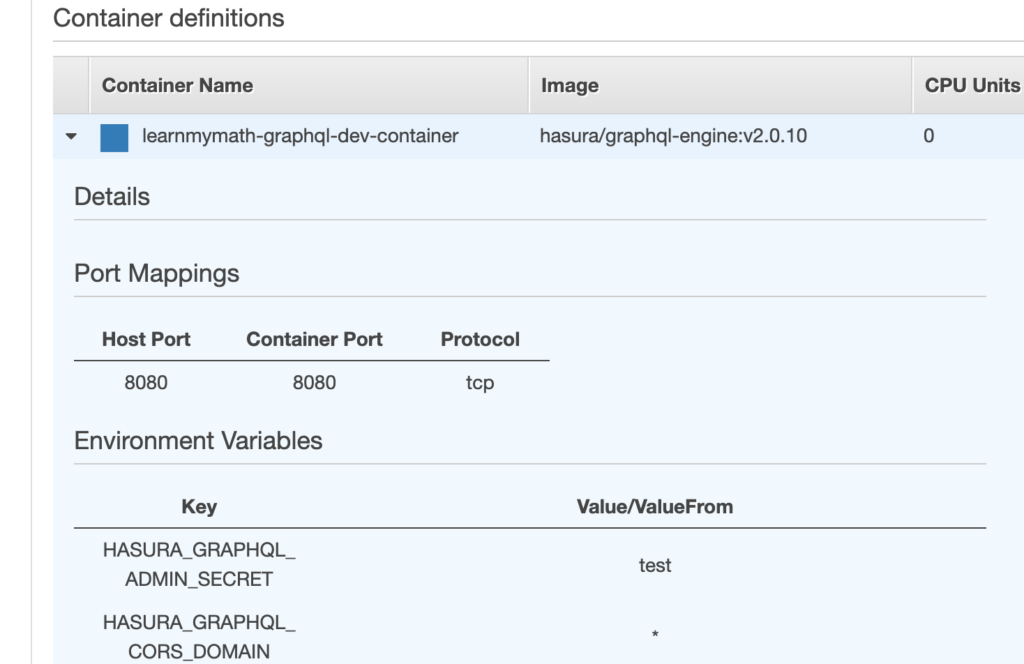
- Environment variables must be present
- Host port and Container port must be the same to work. I tried having container port different from host port and that did not work for me
- Size
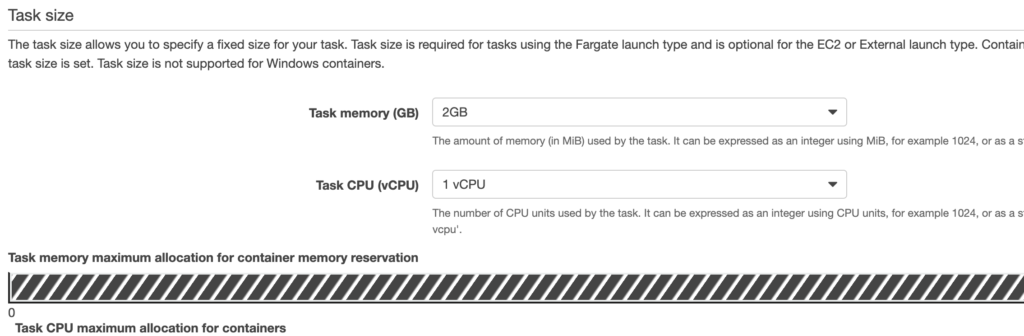
- Leave “Operating system family” alone.
- Leave entrypoint or any command alone.
- Make sure that the ecs execution role has previliges to access other aws parties your app needs. Things such as secret manager, sqs, email, etc.
Create a Service using your Task Definition
- Fill in the Service details
- For security group, create a new security and make sure that group has access to and from database, third party APIs, or other aws services that call your service
- Make sure you only include AZ zones that are allowed by your load balancer.
- Add load balancer
- Add health check /ping
- Allow your server to boot up and be healthy before load balancer starts checking for its health
Hasura – Query
Hasura – Subscription